Corporate governance
A robust corporate governance framework is a key foundation of the Company's sustainable development. CTBC Holding was the first financial holding company in Taiwan to have independent directors comprise more than half of its board members. In addition, the diverse backgrounds of our independent directors and our implementation of a governance philosophy that advocates separating management and ownership rights enable the Board to perform its supervisory duties and conduct business with integrity.
Sound board structure
The Board of Directors of CTBC Holding has seven directors, four of whom are independent directors. In 2018, the Board held 17 meetings, the average attendance rate of which was 96.64%. The average term of office of CTBC Holding's directors is 7.7 years. Each director brings a wealth of relevant experience; of the independent directors, one is a former member of the Financial Supervisory Commission and a current university professor, one is the long-serving chairman of a listed company, one is a lawyer, and the other is a professor with the diverse expertise needed for the operation of the Company, the expertise and experience of whom are highly rated in the industry.
Functional committees supporting supervision
To assist and strengthen the supervisory functions of the Board of Directors, five functional committees have been established, namely the Audit Committee, Remuneration Committee, Risk Management Committee, Nomination Committee, and Ethics and Integrity Committee. Each committee comprises directors and independent directors.

Ethical management
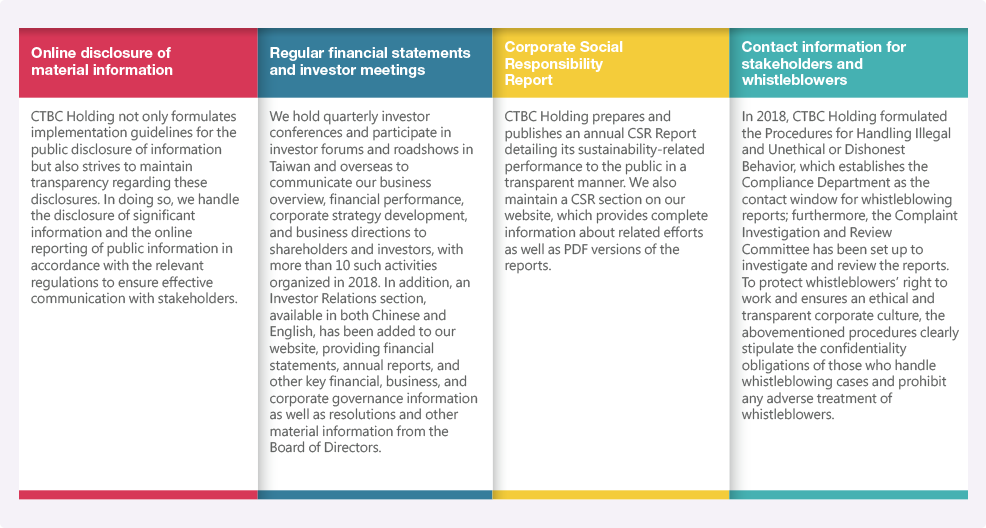
Transparency and ethics are more than means of implementing and demonstrating CSR—they are also means of reducing brand risks, boosting employee morale, and enhancing attractiveness to both local and foreign investors. CTBC Holding has always pursued transparent and ethical corporate governance; it strives to be open and detailed in its information disclosure and to provide a platform for smooth communication among stakeholders.
In 2018, CTBC Holding formulated the Procedures for Handling Illegal and Unethical or Dishonest Behavior, which establishes the Compliance Department as the contact window for whistleblowing reports; furthermore, the Complaint Investigation and Review Committee has been set up to investigate and review the reports. To protect whistleblowers' right to work and ensures an ethical and transparent corporate culture, the abovementioned procedures clearly stipulate the confidentiality obligations of those who handle whistleblowing cases and prohibit any adverse treatment of whistleblowers.
Regulatory compliance
Combating money laundering and terrorist financing
Regulations
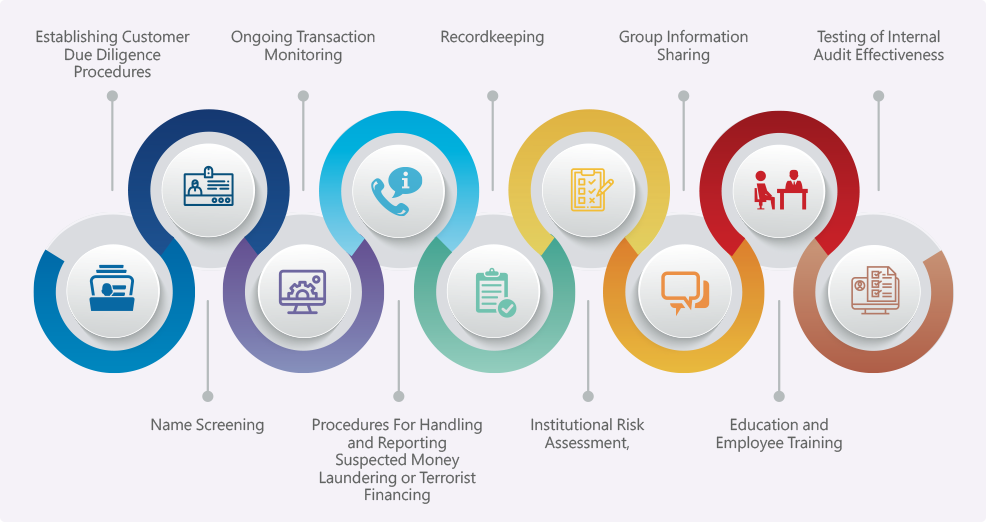
To comply with regulations such as the Money Laundering Control Act, Counter-Terrorism Financing Act, and Regulations Governing Anti-Money Laundering of Financial Institutions, CTBC Holding has established the Anti-Money Laundering and Countering the Financing of Terrorism Policy (Plan); Procedures for Identifying, Measuring, Controlling, Mitigating, Monitoring and Reporting Money Laundering and Terrorist Financing Risks; Procedures for Group Anti-Money Laundering and Countering Terrorist Financing Information-Sharing and Application; Procedures for Counter-Terrorism Financing Act Sanctions List Screening of Persons other than Financial Institution Customers or Related Parties of a Transaction; and Education and Training Measures for Anti-Money Laundering and Combating Terrorist Financing. Our subsidiaries formulate their internal regulations in accordance with these policies and rules as well as the norms, models, and guidelines of the competent authorities and trade associations of various industries. CTBC Bank, Taiwan Life, CTBC Securities, and CTBC Investments have established a joint Anti-Money Laundering and Terrorist Financing Committee to ensure that related risks are properly controlled for.
Education and training
To effectively prevent money laundering and terrorist financing, CTBC Holding actively promotes anti-money laundering education and training. Senior management personnel are required to receive yearly education and training on the topics and all employees must complete regular anti-money laundering courses. In addition, we conduct customized training according to various employees' job functions and actively encourage our employees to participate in anti-money laundering-related training as well as apply for anti-money laundering-related qualifications. These efforts are aimed at ensuring that all members of CTBC Holding, from Board directors to entry level employees, possess the professional capabilities and culture necessary to prevent money laundering and combat terrorist financing. Chairman Wen-Long Yen, together with more than 300 supervisors from CTBC Holding and its subsidiaries, attended the Anti-Money Laundering and Combating the Financing of Terrorism training course in 2018.
Dimensions of anti-money laundering and terrorist financing
Emerging risk identification
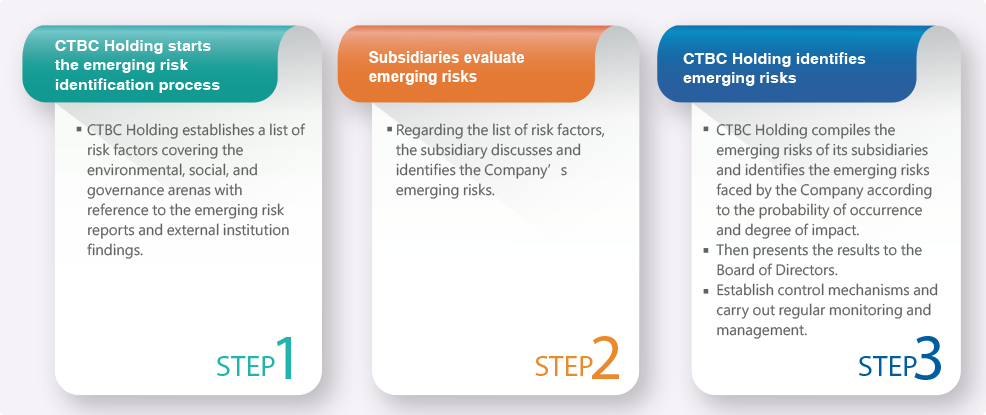
Changes in the overall environment may result in emerging risks that are different from those of the past or otherwise unexpected. The Company has developed an emerging risk identification process to prepare itself for potential challenges that it may face. The emerging risk identification process is used to identify emerging risks, assess the impact of these risks, and develop risk mitigation measures and management mechanisms. The emerging risk identification results are then submitted to the Board of Directors.
Emerging risk identification process
Emerging risk identification results for 2019
| Risk area | Description | Effect on business operations | Mitigation measures/response strategies |
|
Emerging
technologies and information security |
|
|
Major subsidiaries strengthen their control mechanisms as follows:
|
|
Money
laundering and terrorist financing |
The products or services provided by the Company's subsidiaries may be used as a tool or medium for money laundering or terrorist financing to obtain illegal funds, commit criminal activity, and engage in other illicit or improper transactions | Potential legal penalties, resulting in operating and reputational damage and in turn reducing investors' willingness to invest |
|
|
Supervisory
and legislative changes |
Unexpected risks and challenges arising from trends in international supervision and upgrading the depth and breadth of supervision | Potential legal penalties, resulting in operating and reputational damage and in turn reducing investors' willingness to invest |
|
Internal control and auditing
Internal control system
In order to manage its internal control and operating procedures, the Company requires all management units to review, whether their internal procedures are consistent with external laws and regulations, thereby avoiding operational risks and illegal practices. The Company also requires all units to conduct self-evaluations to assess their management's supervision and control over areas such as risk culture, risk identification, control activities and the division of duties, information and communication, supervisory activities, and corrective measures.
Internal control system's three lines of defense
| Units and roles | Functions and responsibilities | ||
| First line |
|
Ensure compliance with risk management regulations and implement daily risk control |
|
| Second line |
|
Establish management systems and monitor the implementation of the first line of defense |
|
| Third line |
|
Independently confirm and evaluate the operation of the internal control system |
|
Internal audit system
CTBC Holding established a General Auditor System in accordance with the Implementation Rules of Internal Audit and Internal Control System of Financial Holding Companies and Banking Industries and set up an internal audit unit directly subordinate to the Board of Directors. The unit conducts its audit activities objectively and impartially and provides recommendations to ensure the proper implementation of the internal control system in order to assist the Board of Directors and management in reviewing and evaluating the effectiveness of the internal control system. The internal audit unit conducts a general business audit of the Company every year and a special business audit on the finance, risk management, and regulatory compliance of the Company and its subsidiaries every six months.
Information security
With the constant evolution of digital financial services and in the face of increasing cybersecurity threats, the Company is emphasizing the critical need for prevention, preparation, and response measures. To this end, we have adopted five main strategies, namely information security management, information security prevention, monitoring and response measures, information gathering and joint defense, and personal information protection, together constituting a comprehensive set of controls. To ensure information security and grant customers peace of mind, CTBC Holding has taken steps to ensure comprehensive control of various aspects of cybersecurity, including establishing organizations and systems, enhancing software and hardware capabilities, implementing education and awareness, executing effective management, and aligning with international standards.
Organization and system establishment
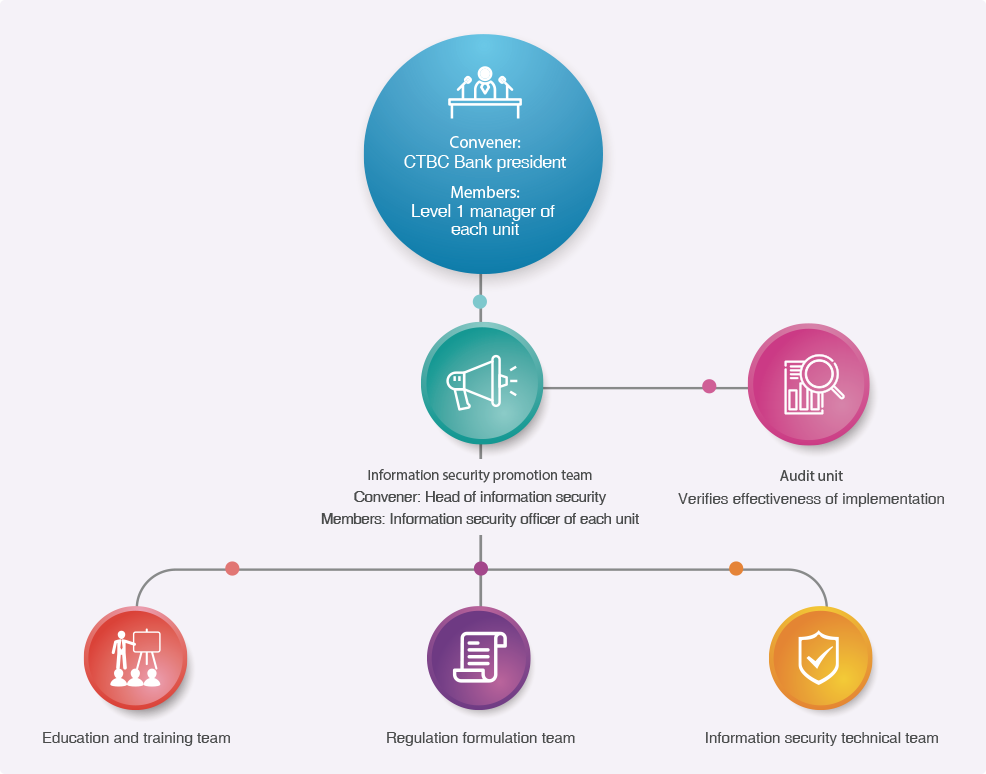
CTBC Bank has formulated an Information Security Policy and set up a Corporate Information Security Committee to serve as the highest authority for its information security operations management. In 2017, the Global Information Security Department, a dedicated unit directly under the management of the Bank's president, was established to develop and improve the organization of the Information Security Department. The Corporate Information Security Committee, with the president as its convener and the head of information security as its executive secretary, oversees the effectiveness of information security management initiatives and emerging information security issues and solutions on a quarterly basis. It passes along important issues to the Board of Directors; the status of information security management operations is also reported to the Board of Directors on an annual basis.
Corporate Information Security Committee organizational chart